Introducing The Art of Threat Modeling for Detection Engineering
BY
Asante Babers
/
Nov 16, 2023
/
Detection Engineering
/
2 Min
Read
Initial Motivations
I’ve spent over ten years in the cybersecurity field. While I’ve delved into various specialties, my insatiable curiosity often led me to seek new challenges. Lately, I’ve found a deep enthusiasm for detection engineering.
Throughout my career, I’ve leveraged the knowledge of others to enhance my journey. Lately, that sentiment hasn’t changed. I operationalize threat research and intelligence of others to build detections.
There are many threat modeling frameworks in information security, and individuals use them to identify viable attack vectors, which leads to detection ideas.
Concerns and the Need for Clarity:
Like many facets of cybersecurity, there are issues in Detection Engineering. So, why address a threat modeling framework first?
We needed a systematic way to identify, sort, and handle threats. This will make it easier for us to spot dangers, boost our effectiveness, improve our security, work better together, and stay ready for evolving threats. - Asante Babers
The Solution? A threat modeling framework for detection engineering.
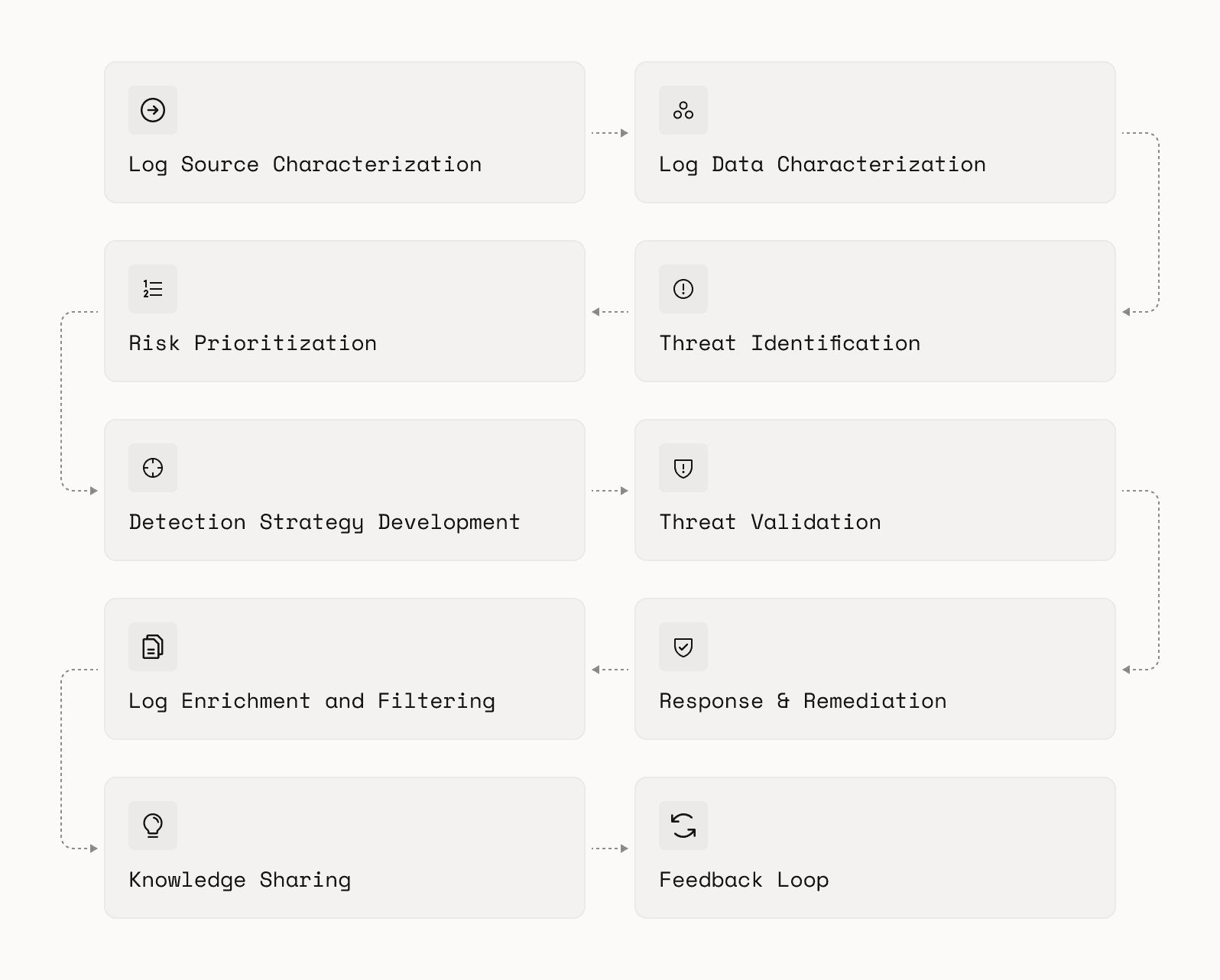
The roots of this framework stem from the one thing that detection engineers must have to operate: logs. By identifying and classifying log sources, we can outline potential attacks that an asset might be exposed to in a shareable model.
You can view the framework at https://github.com/atbabers/DE-ThreatModel.
Summary
This is a ten-step iterative process for threat modeling focused on log sources. I crafted this approach to aid detection engineers in identifying key data and sparking new ideas for detections. Unlike many other frameworks that use acronyms for their steps, the term “Authac” ("pronounced": aw-thak) is not an acronym. Instead, it’s a condensed version of a guiding principle for detection engineers: to authenticate and authorize every action occurring within our organization.
Objectives
Comprehensive Coverage: Ensure detection for a broad range of threat scenarios.
Prioritization: Focus detections on highest likelihood and impactful threats.
Proactive Approach: Anticipate threats and set up detections and response strategies in advance.
Validation Of Controls: Assess and fill gaps in current security measures.
Reduced False Positives: Fine-tune detections to minimize false alarms.
Improved Communication: Foster unified understanding of threats among detection engineers.
Continuous Improvement: Regularly update threat models as risks develop.
Steps